When a developer writes, compiles and links a programme it may be stored on a computer disk as a file in the disk file system. This file is created in a predefined format that the operating system or operating system shell will recognise as an executable programme.
When a programme is run it is instantiated in memory, taking up system resources such as memory for data structures, file descriptors and providing at least one thread of execution which defines the current state and subsequent required operations for the process. The current executing program, or process, has total use of the microprocessor while in it's run state. A process will use files within the filesystems and may access the physical devices in the system either directly or indirectly.
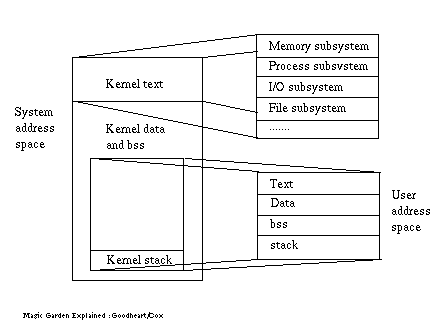
A process may operate in one of two modes which are known as 'user' mode and 'system' mode (or kernel mode). A single process may switch between the two modes, i.e. they may be different phases of the same process. Processes defaulting to user mode include most application processes, these are executed within an isolated environment provided by the operating system such that multiple processes running on the same machine cannot interfere with each other's resources. A user processs switches to kernel mode when it makes a system call, generates an exception (fault) or when an interrupt occurs (e.g. system clock). At this point the kernel is executing on behalf of the process. At any one time during its execution a process runs in the context of itself and the kernel runs in the context of the currently running process. This is shown in Figure 1.

Processes operating in kernel mode are privileged and are granted access to all computer resources (such as all available memory) free of the restrictions applied to user mode processes. The distinction between a process in either user or kernel mode may be supported by the hardware which serves to enforce the privilege rule and so protect the computer system from undue damage or failure due to ill behaved user processes.
Though the basic concepts are similar, different operating systems implement process management in different ways.
| Linux | Windows NT | |
| On the Linux operating system
privileged services are largely implemented by a single monolithic kernel.
The kernel provides the central services required to support the successful
operation of the computer.
The Linux kernel can also have a number of loadable modules which may serve to supplement its central functions e.g. by the addition of a new file system. As the kernel carries out a number of responsibilities within a single entity it is commonly known as a macrokernel architecture. |
The Windows NT operating system
is based on a derivative of a layered operating system (such as VAX VMS)
and a true client/server operating (such as Mach) microkernel architecture,
where the central kernel process carries out only the most basic tasks
in the most efficient manner possible.
Associated with the microkernel are a number of privileged processes collectively known as the Executive which operate in their own separate process subsystems. These includes (amongst others) a dedicated Process Manager, Object Manager and Virtual Memory manager to provide specialised services as required to support the establishment of processes and their resources. |
Every user process runs in its own address space
(typically 3Gbytes on a 32 bit processor) isolated from the address space
of other active processes. From the point of view of the individual process
it also has complete access to the processor(s) of the machine on which
it is running i.e. it has it's own virtual machine on which it runs,
under the control of the operating system but independent from other processes.